Secure the connection with certificates
As you connect to the gateway remotely, security concerns come to mind. If your gateways are installed in a trusted network (close network, VPN, ...) this may already be solved, but if they are connected through other networks you will want to secure the connection.
The gateway propose a simple and powerful way to both authenticate the device and encrypt the connection : TLS certificates.
Having a valid and trusted certificate
The various systems (Android, Windows, web browsers, ...) will, by default, either trust a certificate or not trust it. This depends on the type of system and how it is configured. Generally speaking, the systems will trust valid certificates that have a trusted root certificate authority. Each system has his set of trusted root certificate authorities.
If the certificate it trusted, this means the system will agree that the certificate's emitter is who it pretends to be.
Untrusted certificate limitations
If the certificate is not trusted by a system, it will generally forbid access to security sensitive features. For example, Chrome will not let a website with a non-trusted certificate access the position, or the clipboard.
In some cases, and depending the system's security policy, the user will also have the choice to manually trust the certificate.
Even if a certificate is not trusted by the system, it will still be used for encryption when using https. Meaning that your data will stay confidential.
Regarding security, you can securely use an untrusted certificate if you trust the emitter on your own.
Web browser certificates validity
Web browsers may warn you if the certificate is not valid when accessing through http :
| Browser | Navigation bar overview |
|---|---|
| Chrome |
|
| Firefox |
|
| Edge |
|
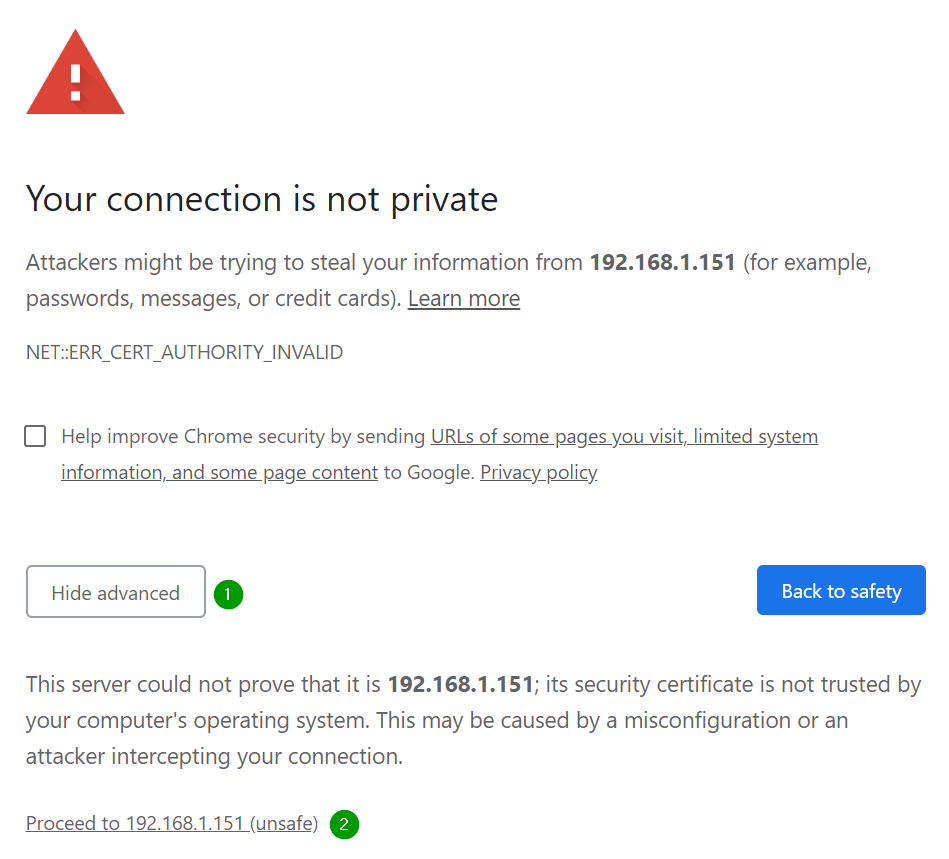
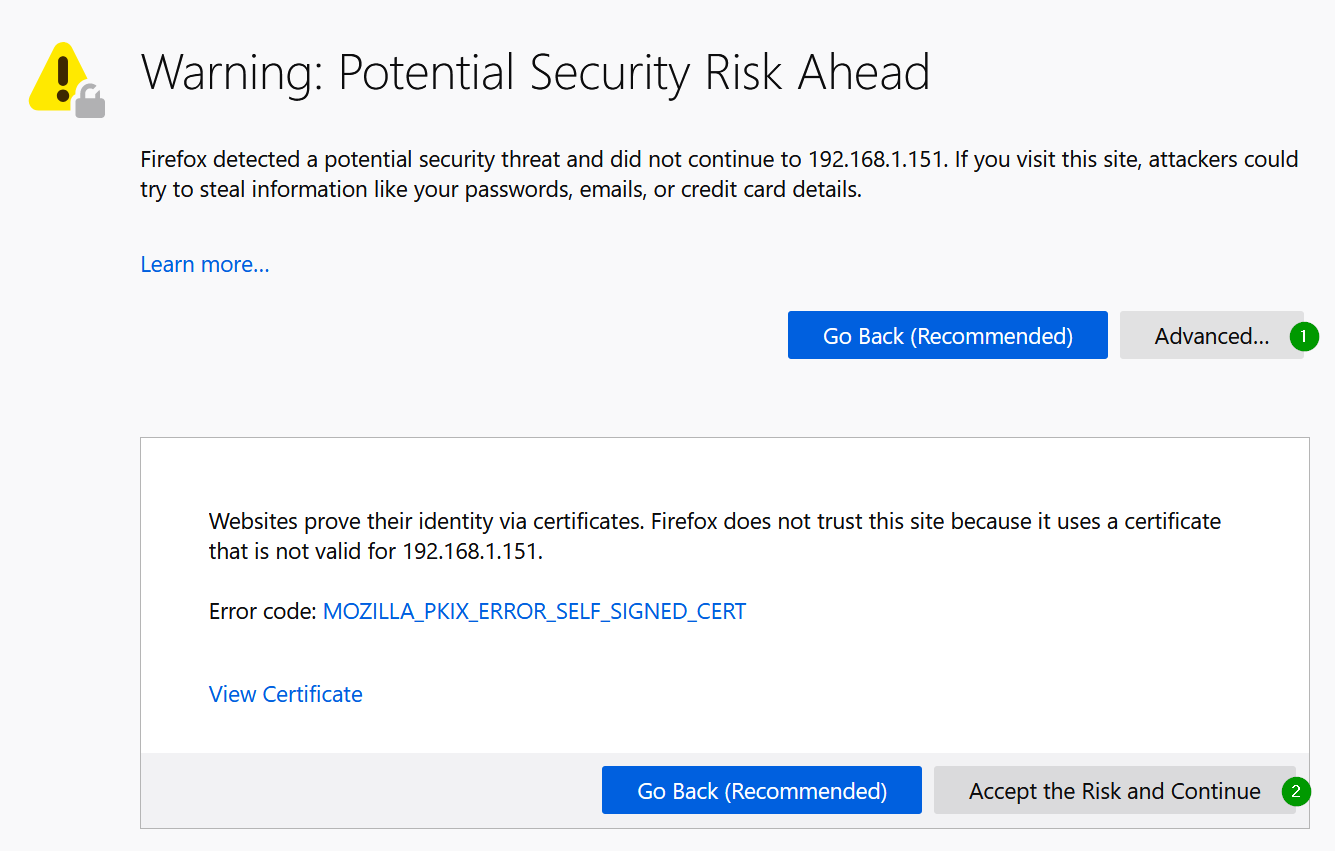
When accessing through https, the warning is more visible:
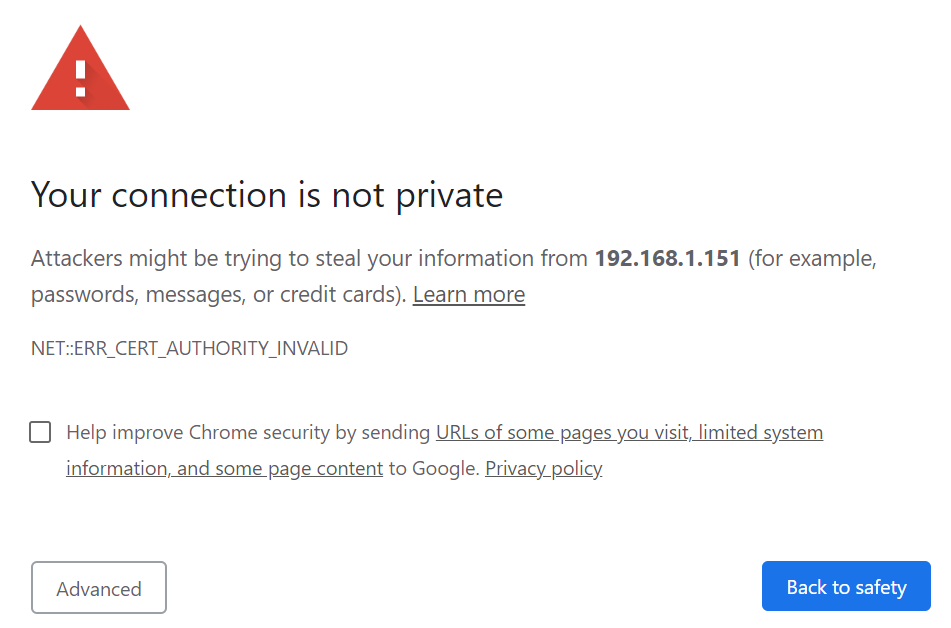
In both cases, the browser tells you that the emitter of the page (the gateway) could not prove that he is who he pretends to be. If you trust the source, you can bypass the warnings.
Update the certificate
The gateway needs a private certificate with the certificate key as it is the certificate that will be used to encrypt the outgoing data.
Choose a certificate
Default certificate
A default certificate is generated at the first boot of the gateway. As the certificate is generated on the gateway itself, it's called a "self signed" certificate. These kind of certificate are not trusted by default by various other systems.
Generated certificate
From the GUI Manager preferences page, you can also generate a new certificate. It will be the same kind of certificate than the default, but you can add your personal or company details. This will still be a generally untrusted certificate.
Company certificate
You can also upload your own certificate to the gateway. This means you can use certificates generated by your company. This is typically useful if you generate a certificate for each of your gateway that has the company certificate as root trusted certificate. This way, adding the root certificate of your company as trusted certificate of own desktop computer will automatically trust the child certificates.
The web browsers usually require two conditions to be met for a certificate to be considered as valid: it must be emitted by a trusted root CA, and the domain (SAN) of the certificate has to match the accessed domain. This means that to use a company certificate, you must set up a DNS that will give access to the gateways individually and that the domain name (e.g. 0b6866.loragw.acme.com ) is part of the certificate SAN. You cannot use the IP to access it.
It's better not to use the same certificate for all your devices. If you have to revoke a certificate, you will have to change the certificate at any place it has been used.
Never put an important certificate into the gateway. Always use a certificate with a low incidence if it gets stolen. Keep in mind that malicious people may, in the worst case, physically access your gateway and recover the private certificate directly from the NAND.
Install the certificate on the gateway
You can upload a new certificate from the GUI Manager preferences page.
The certificates are stored at /etc/manager/certs and /etc/manager/keys.
You can either replace theses files and restart the manager, or add additional files and change the paths in the manager configuration file /etc/manager/config.yml:
# The API allows remote access to the gateway for monitoring and control. Is is used by the Manager web GUI. Authentication is always needed.
api:
http:
[...]
https:
[...]
# When using the secured interface, you must provide a certificate and a key that will be used for data encryption. Use a PEM encoded certificate and key.
certificateFilePath: /etc/manager/certs/default.crt
keyFilePath: /etc/manager/keys/default.key
The active certificate and key will be overridden when a new certificate is generated, and this even if you change the path in the config file. If you don't have a copy of the certificate, create a backup when you install it.
Restart the manager
Once the new certificate installed, you must restart the manager to use the new certificate:
sudo rc-service managerd restartYou can also restart the gateway if it is allowed to go offline.
When a new certificate is used and this certificate is not trusted (and you connect through https), you may get again the security warnings. The manager GUI will not show these warning until the application is totally reloaded. If you don't recover connection to the gateway, juste refresh the GUI page with F5.